Continuous Threat Exposure Management (CTEM): Why CISOs Are Replacing Periodic Security With Continuous Security Intelligence
Executive Summary
Security tools have evolved, attackers have evolved faster.
Enterprises that still rely on quarterly penetration tests and annual audits are operating with a false sense of security. This is why Gartner calls CTEM (Continuous Threat Exposure Management) one of the most critical cybersecurity trends for 2026.
CTEM shifts organizations from static vulnerability scanning to continuous, intelligence-driven exposure management aligning security with how attackers operate.
1. The Problem with Traditional Cybersecurity Programs
Most enterprises secure themselves based on:
- Assumed attack paths
- Annual audits
- Point-in-time scans
- Generic control frameworks
But threat actors don’t operate annually. They operate continuously.
They exploit configuration drifts, real-time identity weaknesses, misaligned cloud policies, exposed APIs, ungoverned shadow AI usage.
CTEM solves this by turning cybersecurity into a real-time operational discipline.
2. What CTEM Actually Is and Isn’t
CTEM is not another tool, platform, or dashboard. It is a programmatic approach that enables enterprises to identify, validate, prioritize, and remediate the exposures that matter most right now.
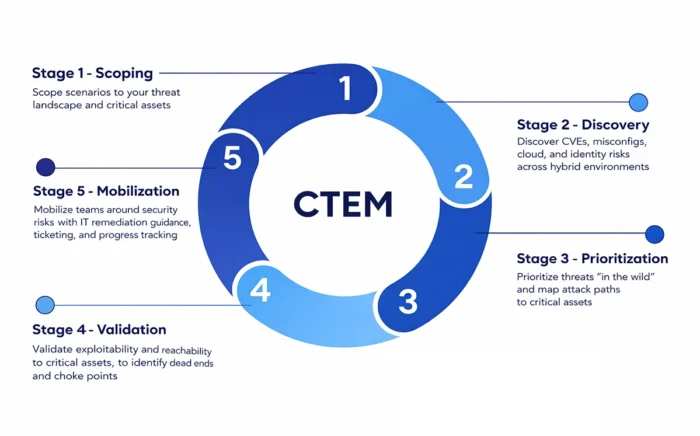
The CTEM cycle:
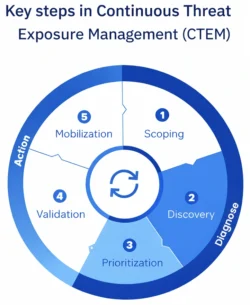
1. Scoping
Define attack surfaces dynamically, cloud, identity, SaaS, APIs, OT.
2. Discovery
Continuously map how assets behave, drift, and interact.
3. Prioritization
Rank exposures based on exploitability, not severity labels.
4. Validation
Simulate attacker behavior using AI + automated red teaming.
5. Mobilization
Convert exposure insights into operational workflows.
3. Why CISOs Are Making CTEM a 2026 Budget Priority
✔ Because vulnerabilities ≠ exposures
A vulnerability becomes an exposure only if it can be reached, exploited, and chained.
Traditional scanners overwhelm teams. CTEM highlights only what is actually dangerous.
✔ Because cloud-native enterprises have fluid attack surfaces
Identity drift, misconfigured IAM policies, unencrypted storage buckets, unmanaged API gateways, these can emerge within hours.
CTEM detects and tests these continuously.
✔ Because AI adoption creates new attack vectors
Enterprises deploying LLMs now face prompt injection, data exfiltration via model responses, model poisoning, shadow AI usage, misaligned GenAI access permissions.
CTEM frameworks embed AI-specific exposure analysis.
✔ Because compliance is shifting toward continuous assurance
Regulators in BFSI, healthcare, and telecom are moving toward models where security posture must be visible in real time.
CTEM becomes the operational backbone.
4. How Leading Enterprises Implement CTEM (The Modern Approach)
Competitors like Palo Alto, Wiz, Tenable, IBM, and Accenture have already repositioned their security offerings around CTEM.
The most successful implementations share four principles:
1. Identity Becomes the New Perimeter
Continuous identity threat detection becomes non-negotiable.
2. Attack Path Analysis Drives Remediation
Fix what leads to breach not every alert.
3. Automated Red Teaming Replaces Manual Pentesting
AI-generated attack simulations dramatically reduce exposure windows.
4. CTEM Integrates with DevSecOps & CloudOps
Security is no longer an escalation. It becomes an automated workflow.
5. PureSoftware POV: CTEM as the Security Operating System for 2026
PureSoftware helps organizations operationalize CTEM by enabling:
- Continuous cloud exposure monitoring
- Identity threat detection
- Automated attack path simulation
- SaaS & API surface governance
- AI/GenAI attack vector assessment
- Risk-based remediation workflows
- Executive dashboards for exposure readiness
Conclusion
CTEM is not the future of cybersecurity, it is the new baseline. Enterprises that adopt it early will experience fewer breaches, faster recovery, and significantly stronger cyber resilience.
Frequently Asked Questions
-
How is CTEM different from vulnerability management?
CTEM focuses on exposures, vulnerabilities that can be reached, exploited, and chained not all vulnerabilities. -
Who owns CTEM: Security or Operations?
Security leads it, but CTEM becomes an enterprise-wide operational discipline embedded across DevOps, CloudOps, and Risk. -
How fast can organizations implement CTEM?
Pilot in 8–12 weeks, full deployment in phases aligned to cloud maturity.

