Operationalizing Data Privacy: From Policy to Practice
Why Operationalizing Data Privacy Has Become Essential
Operationalizing data privacy is no longer a theoretical discussion for enterprises; it is a practical necessity. Most organizations today already have privacy policies, compliance frameworks, and regulatory controls in place. Yet despite this, privacy incidents, data exposure, and regulatory scrutiny continue to rise. The reason is not a lack of intent or awareness. It is the growing gap between policy and practice.
As enterprises scale across cloud platforms, SaaS applications, APIs, analytics environments, and AI systems, data moves continuously across organizational boundaries. Privacy cannot rely on periodic reviews or static documentation in such environments. It must operate every time data is accessed, shared, or transformed. This is what it truly means to operationalize data privacy.
The Policy–Practice Gap in Enterprise Data Privacy
Traditional privacy programs often break down during execution.
Common challenges include:
- Sensitive data distributed across multiple systems without real-time visibility
- Access permissions that accumulate over time and are rarely revoked
- Governance controls applied after deployment rather than embedded into systems
According to research from McKinsey & Company, organizations operating in highly distributed digital environments face increased risk when governance and visibility fail to scale with data growth particularly across cloud and analytics platforms. Similarly, Gartner has consistently highlighted that identity-centric controls and continuous governance are essential for modern data protection strategies. These findings point to a critical insight: data privacy failures are usually operational, not accidental.
What Does It Mean to Operationalize Data Privacy?
Operationalizing data privacy means ensuring privacy is enforced by design and by default, not just during audits. Instead of asking: “Do we have the right policies?” Organizations must ask: “Does privacy operate continuously across our systems and workflows?”
A true data privacy operating model ensures that:
- Privacy adapts as systems change
- Controls scale with data growth
- Exposure is detected early, not after impact
This requires embedding privacy directly into the organization’s cybersecurity foundation.
The Data Privacy Operating Model
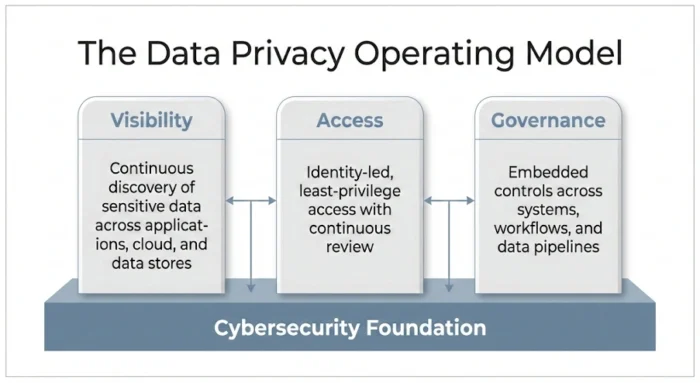
1. Continuous Visibility Across the Data Landscape
Operationalizing data privacy starts with visibility. Enterprises must continuously understand:
- What sensitive data exists
- Where it resides across environments
- How it flows between systems and teams
Static data inventories quickly become outdated in modern environments. Continuous discovery, classification, and monitoring are essential to reducing blind spots and unmanaged exposure. Without visibility, privacy controls become assumptions rather than safeguards.
2. Identity-Led Access Control
In distributed digital ecosystems, identity has become the most effective control plane for enterprise data privacy. Operationalized privacy depends on:
- Identity-led access control
- Least-privilege enforcement
- Continuous access validation based on real usage
By aligning access decisions with identity context, organizations significantly reduce internal exposure, one of the most common contributors to privacy incidents. This approach also strengthens alignment between identity security and data governance.
3. Embedded Governance and Privacy by Design
Privacy governance cannot operate outside the technology stack. To scale effectively, governance must be embedded into:
- Application architectures
- Data pipelines and workflows
- Cloud and API interactions
- AI and analytics environments
When governance operates continuously within cybersecurity systems, organizations can detect misuse, policy drift, and exposure as it happens, rather than after damage has occurred. This transforms data privacy from a reactive process into a living capability.
Why Cybersecurity Is Central to Operationalizing Data Privacy
Operationalizing data privacy is not possible without cybersecurity. Cybersecurity provides the mechanisms needed to:
- Monitor data activity continuously
- Enforce identity-based access
- Detect exposure early
- Apply governance consistently across environments
This is why cybersecurity and data protection must be treated as inseparable disciplines.
At PureSoftware, data privacy is approached as a cybersecurity-enabled capability, helping enterprises reduce exposure while enabling secure digital scale.
Final Takeaway
Operationalizing data privacy is the next stage of maturity for enterprises navigating complex digital ecosystems. Organizations that embed privacy into cybersecurity operations will be better positioned to manage risk, maintain trust, and scale securely not just during audits, but every day.
Frequently Asked Questions
-
What does operationalizing data privacy mean?
Embedding privacy controls into systems and workflows so privacy operates continuously, not periodically. -
How is this different from compliance-driven privacy?
Compliance focuses on meeting regulations; operational privacy focuses on reducing real-world exposure. -
Why is identity-led access critical?
It ensures access permissions align with real usage, reducing excessive access and internal risk. -
How does cybersecurity support data privacy?
Cybersecurity enables visibility, monitoring, access control, and governance enforcement at scale. -
Is this approach only relevant for large enterprises?
No. Any organization operating across cloud, SaaS, or data platforms benefits from operational privacy models.

