Data Privacy in 2026: Why Legacy Models Are No Longer Enough
Data privacy in 2026 is no longer defined by policies or regulatory checklists alone. As digital ecosystems expand across cloud platforms, SaaS applications, APIs, AI models, and partner networks, organizations must rethink how data privacy operates within their cybersecurity framework.
In 2026, the challenge is not the absence of privacy policies.
It is the gap between documented intent and real-world data exposure.
Modern enterprises need a modern data privacy strategy, one that aligns data privacy directly with cybersecurity and data protection capabilities, rather than treating it as a separate compliance function.
Why Traditional Data Privacy Models Are Failing in 2026
Most traditional data privacy programs were designed for environments where:
- Data lived in a limited number of systems
- Access paths were predictable
- Ownership was clearly defined
That reality no longer exists. In data privacy in 2026, sensitive data continuously moves across:
- Cloud environments
- Enterprise applications
- Analytics platforms
- AI and machine learning pipelines
Yet many organizations still rely on static data inventories, periodic audits, and manual access reviews. These legacy controls validate intent but fail to surface continuous exposure. This is where data privacy intersects directly with modern cybersecurity. Without continuous visibility and control, privacy risk accumulates silently through excessive access, misconfigurations, and governance gaps.
How Modern Cybersecurity Enables Data Privacy in 2026
Effective data privacy in 2026 is inseparable from cybersecurity. Organizations that mature their privacy posture do so by strengthening three core cybersecurity-aligned foundations.
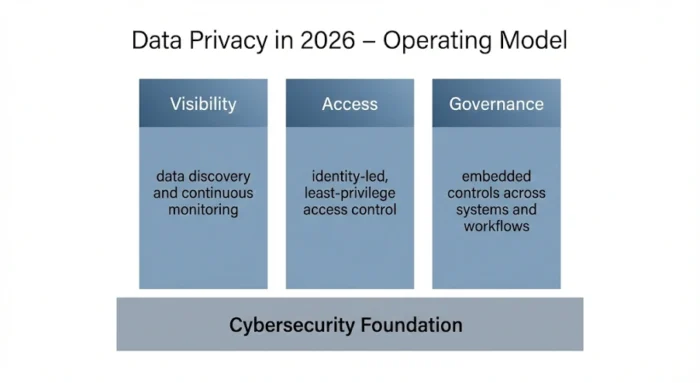
1. Continuous Visibility Across the Data Landscape
Modern data privacy begins with visibility.
Organizations must continuously understand:
- What sensitive data exists
- Where it resides
- How it moves across systems
Static data maps quickly become obsolete. Continuous discovery and classification supported by enterprise cybersecurity frameworks are essential to reducing blind spots.
This level of visibility forms the backbone of scalable enterprise data protection.
2. Identity-Led Access Control as a Privacy Control Plane
In 2026, identity is the most critical control layer for data governance and privacy. Leading organizations move beyond role-based access to:
- Identity-led access control
- Least-privilege enforcement
- Continuous access validation
By aligning access decisions with identity context and usage patterns, organizations significantly reduce internal exposure, one of the most common causes of privacy incidents. This approach tightly integrates identity security with data privacy outcomes.
3. Embedded Governance Through Privacy by Design
Privacy by design is no longer optional. In data privacy in 2026, governance must be embedded into:
- Application architectures
- Data pipelines
- Cloud and API interactions
- AI and analytics workflows
When governance is operationalized within cybersecurity systems, organizations can detect policy drift, misuse, and exposure in near real time rather than after impact. This transforms privacy from a reactive process into a continuously operating capability.
From Compliance to Cybersecurity-Led Data Privacy
One of the biggest shifts in data privacy in 2026 is its repositioning within the enterprise. Privacy is no longer just a legal or compliance concern.
It is a cybersecurity-led business capability.
Organizations that integrate data privacy into their cybersecurity strategy are better equipped to:
- Scale digital transformation securely
- Manage regulatory risk proactively
- Enable responsible AI adoption
- Build long-term trust with customers and partners
This is where PureSoftware’s cybersecurity approach becomes relevant bringing together visibility, identity, governance, and continuous monitoring to support data protection at scale.
What Leaders Should Prioritize for Data Privacy in 2026
Rather than adding more tools or policies, leaders should ask:
- Do we have continuous visibility into sensitive data?
- Is access governed by identity and real usage patterns?
- Is data governance embedded into system design?
- Can our cybersecurity controls detect exposure early?
Organizations that address these questions directly are better positioned to operationalize data privacy in 2026.
Closing Perspective
Data privacy in 2026 will not be measured by how many policies an organization maintains.
It will be measured by how effectively privacy operates within its cybersecurity ecosystem across data, identities, and systems, every day.
Enterprises that modernize now will move beyond compliance and toward sustainable, trusted digital growth.
Frequently Asked Questions
-
What makes data privacy in 2026 different from earlier years?
Data privacy in 2026 must account for distributed data, cloud-native architectures, and AI-driven systems, requiring continuous controls rather than static compliance measures. -
How does cybersecurity support data privacy?
Cybersecurity provides the visibility, identity controls, and governance mechanisms needed to enforce data privacy across modern digital environments. -
Why is identity-led access control critical for data privacy?
Identity-led access control ensures data access is continuously evaluated, reducing excessive permissions and internal exposure. -
Is compliance still relevant for data privacy in 2026?
Yes, but compliance alone is insufficient. Effective data privacy in 2026 requires operational cybersecurity controls that work continuously. -
How does PureSoftware approach data privacy?
PureSoftware aligns data privacy with cybersecurity and data protection capabilities to help organizations manage exposure and build trust at scale.

